Table of Contents
Introduction
IDM replica is the same copy of the existing master IDM server. The use of a replica is to have multiple copies of master and it can be used in different geographical location. RHEL 8 replicas only work with IDM masters running on RHEL 7.4 and later, Moreover, the master server should be installed on RHEL 8 and installed with IDM 4.x packages. The steps to follow for previous versions are similar to the below guide but little different from the current one.
IDM Related Articles
- Setup and Identity Management server in Linux using IPA
- Creating our 1st DNS zones and DNS record in IPA Server
- Integrating IDM with AD (Active directory) using indirect cross-forest trust
- Setup a Linux server as IDM client to authenticate with Active Directory
- Setup a FreeIPA or IDM Replica
Setting up as Client
Before setting up IDM replica first we need to join the node as a client with IDM server by running ipa-client-install. To install the required packages use yum to install client packages.
# yum install ipa-client -yRun the install command it will auto-discover the IPA server information.
# ipa-client-installOutput for reference
[root@idm2 ~]# ipa-client-install
This program will set up IPA client.
Version 4.8.0
Discovery was successful!
Do you want to configure chrony with NTP server or pool address? [no]:
Client hostname: idm2.lincls.linuxsysadmins.local
Realm: LINCLS.LINUXSYSADMINS.LOCAL
DNS Domain: lincls.linuxsysadmins.local
IPA Server: idm1.lincls.linuxsysadmins.local
BaseDN: dc=lincls,dc=linuxsysadmins,dc=local
Continue to configure the system with these values? [no]: yes
Synchronizing time
No SRV records of NTP servers found and no NTP server or pool address was provided.
Using default chrony configuration.
Attempting to sync time with chronyc.
Time synchronization was successful.
User authorized to enroll computers: admin
Password for admin@LINCLS.LINUXSYSADMINS.LOCAL:
Successfully retrieved CA cert
Subject: CN=Certificate Authority,O=LINCLS.LINUXSYSADMINS.LOCAL
Issuer: CN=Certificate Authority,O=LINCLS.LINUXSYSADMINS.LOCAL
Valid From: 2020-02-26 20:45:04
Valid Until: 2040-02-26 20:45:04
Enrolled in IPA realm LINCLS.LINUXSYSADMINS.LOCAL
Created /etc/ipa/default.conf
Configured sudoers in /etc/authselect/user-nsswitch.conf
Configured /etc/sssd/sssd.conf
Configured /etc/krb5.conf for IPA realm LINCLS.LINUXSYSADMINS.LOCAL
Systemwide CA database updated.
Hostname (idm2.lincls.linuxsysadmins.local) does not have A/AAAA record.
Missing reverse record(s) for address(es): 192.168.0.21, 2001:8f8:172d:8f0b:e194:b02e:b942:14ee.
Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub
Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub
WARNING: The configuration pre-client installation is not managed by authselect and cannot be backed up. Uninstallation may not be able to revert to the original state.
SSSD enabled
Configured /etc/openldap/ldap.conf
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config
Configuring lincls.linuxsysadmins.local as NIS domain.
Client configuration complete.
The ipa-client-install command was successful
[root@idm2 ~]# Ports Requirement and Firewall
Add the firewall as a service, else use the port number as shown in trailing steps.
# firewall-cmd --add-service={freeipa-4,freeipa-ldap,freeipa-ldaps,freeipa-replication,freeipa-trust} --permanent
# firewall-cmd --reload
# firewall-cmd --list-all[root@idm2 ~]# firewall-cmd --add-service={freeipa-4,freeipa-ldap,freeipa-ldaps,freeipa-replication,freeipa-trust} --permanent
success
[root@idm2 ~]#
[root@idm2 ~]# firewall-cmd --reload
success
[root@idm2 ~]#
[root@idm2 ~]#
[root@idm2 ~]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: ens18
sources:
services: cockpit dhcpv6-client freeipa-4 freeipa-ldap freeipa-ldaps freeipa-replication freeipa-trust ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
[root@idm2 ~]#Or add using the port number which required for IDM replica.
# firewall-cmd --runtime-to-permanent --add-port={80/tcp,443/tcp,389/tcp,636/tcp,88/tcp,88/udp,464/tcp,464/udp,53/tcp,53/udp,123/udp}Installing the Server Packages
In my setup, I’m about to use certificate authority and DNS in my IDM replica. However, Kerberos also should reside on multiple servers as per recommendation from the official guide.
RHEL 7 / CentOS 7 servers
# yum install ipa-server ipa-server-dns bind bind-dyndb-ldap ipa-server-trust-ad -yRHEL 7 / CentOS 8 server
# yum module enable idm:DL1 -y
# yum module install idm:DL1/{dns,adtrust} -yCheck the Connectivity
Check the connectivity to IDM master server from the new IDM replica.
# ipa-replica-conncheck --master idm1.lincls.linuxsysadmins.local[root@idm2 ~]# ipa-replica-conncheck --master idm1.lincls.linuxsysadmins.local
Check connection from replica to remote master 'idm1.lincls.linuxsysadmins.local':
Directory Service: Unsecure port (389): OK
Directory Service: Secure port (636): OK
Kerberos KDC: TCP (88): OK
Kerberos Kpasswd: TCP (464): OK
HTTP Server: Unsecure port (80): OK
HTTP Server: Secure port (443): OK
The following list of ports use UDP protocol and would need to be
checked manually:
Kerberos KDC: UDP (88): SKIPPED
Kerberos Kpasswd: UDP (464): SKIPPED
Connection from replica to master is OK.
Start listening on required ports for remote master check
Listeners are started. Use CTRL+C to terminate the listening part after the test.
Please run the following command on remote master:
/usr/sbin/ipa-replica-conncheck --replica idm2.lincls.linuxsysadmins.local
[root@idm2 ~]#Same time back to IDM server run the check by copying the command from the above output.
# /usr/sbin/ipa-replica-conncheck --replica idm2.lincls.linuxsysadmins.local[root@idm1 ~]# /usr/sbin/ipa-replica-conncheck --replica idm2.lincls.linuxsysadmins.local
Check connection from master to remote replica 'idm2.lincls.linuxsysadmins.local':
Directory Service: Unsecure port (389): OK
Directory Service: Secure port (636): OK
Kerberos KDC: TCP (88): OK
Kerberos KDC: UDP (88): OK
Kerberos Kpasswd: TCP (464): OK
Kerberos Kpasswd: UDP (464): OK
HTTP Server: Unsecure port (80): OK
HTTP Server: Secure port (443): OK
Connection from master to replica is OK.
[root@idm1 ~]# Once we get the above output we are good with the required ports to reach the IDM replica from our master.
Setup the Replica
While setting up the IDM replica we do not require to use --ca-cert-file option. By running the ipa-replica-install utility it will pull the certificate information automatically from the IDM master server.
# ipa-replica-install --principal admin --admin-password Redhat@123 --no-host-dns --setup-ca --setup-dns --no-forwarders --force-joinOutput for reference
[root@idm2 ~]# ipa-replica-install --principal admin --admin-password Redhat@123 --no-host-dns --setup-ca --setup-dns --no-forwarders --force-join
Configuring client side components
This program will set up IPA client.
Version 4.8.0
Discovery was successful!
Client hostname: idm2.lincls.linuxsysadmins.local
Realm: LINCLS.LINUXSYSADMINS.LOCAL
DNS Domain: lincls.linuxsysadmins.local
IPA Server: idm1.lincls.linuxsysadmins.local
BaseDN: dc=lincls,dc=linuxsysadmins,dc=local
Synchronizing time
No SRV records of NTP servers found and no NTP server or pool address was provided.
Using default chrony configuration.
Attempting to sync time with chronyc.
Time synchronization was successful.
Successfully retrieved CA cert
Subject: CN=Certificate Authority,O=LINCLS.LINUXSYSADMINS.LOCAL
Issuer: CN=Certificate Authority,O=LINCLS.LINUXSYSADMINS.LOCAL
Valid From: 2020-02-26 20:45:04
Valid Until: 2040-02-26 20:45:04
Enrolled in IPA realm LINCLS.LINUXSYSADMINS.LOCAL
Created /etc/ipa/default.conf
Configured sudoers in /etc/authselect/user-nsswitch.conf
Configured /etc/sssd/sssd.conf
Configured /etc/krb5.conf for IPA realm LINCLS.LINUXSYSADMINS.LOCAL
Systemwide CA database updated.
Hostname (idm2.lincls.linuxsysadmins.local) does not have A/AAAA record.
Missing reverse record(s) for address(es): 192.168.0.21, 2001:8f8:172d:8f0b:e194:b02e:b942:14ee.
Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub
Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub
SSSD enabled
Configured /etc/openldap/ldap.conf
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config
Configuring lincls.linuxsysadmins.local as NIS domain.
Client configuration complete.
The ipa-client-install command was successful
Warning: skipping DNS resolution of host idm2.lincls.linuxsysadmins.local
Warning: skipping DNS resolution of host idm1.lincls.linuxsysadmins.local
Lookup failed: Preferred host idm2.lincls.linuxsysadmins.local does not provide DNS.
Run connection check to master
Connection check OK
Disabled p11-kit-proxy
Configuring directory server (dirsrv). Estimated time: 30 seconds
[1/41]: creating directory server instance
Starting installation…
Created symlink /etc/systemd/system/multi-user.target.wants/dirsrv@LINCLS-LINUXSYSADMINS-LOCAL.service → /usr/lib/systemd/system/dirsrv@.service.
Opening SELinux policy "//etc/selinux/targeted/policy/policy.31"
Successfully opened SELinux policy "//etc/selinux/targeted/policy/policy.31"
Allocate local instance with ldapi://%2fvar%2frun%2fslapd-LINCLS-LINUXSYSADMINS-LOCAL.socket
[2/41]: configure autobind for root
[3/41]: stopping directory server
[4/41]: updating configuration in dse.ldif
[5/41]: starting directory server
[11/11]: starting directory server
Done.
[7/7]: configuring ipa-dnskeysyncd to start on boot
Done configuring DNS key synchronization service (ipa-dnskeysyncd).
Restarting ipa-dnskeysyncd
Restarting named
Updating DNS system records
Global DNS configuration in LDAP server is empty
You can use 'dnsconfig-mod' command to set global DNS options that
would override settings in local named.conf files
The ipa-replica-install command was successful
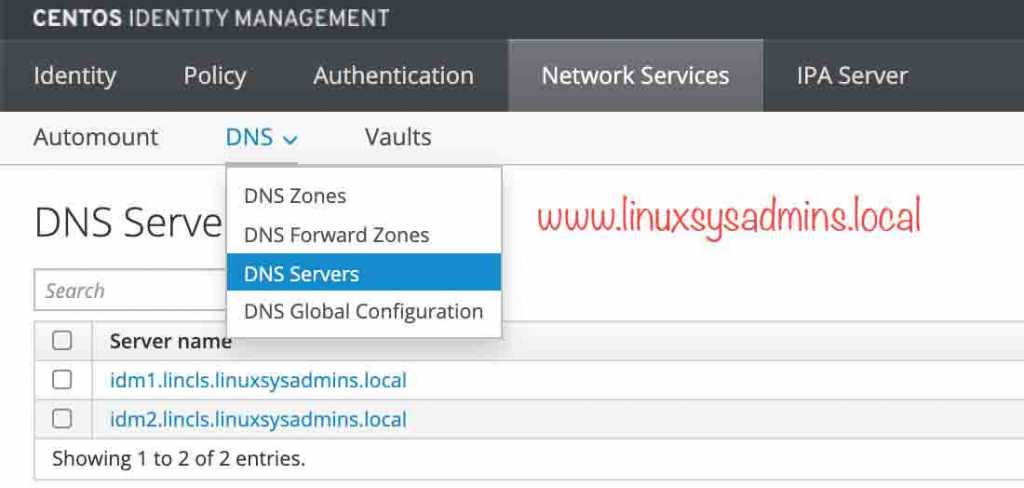
[root@idm2 ~]#That’s it, Now we should get two DNS, CA servers list in the master side.
Network Services –> DNS –> DNS Servers
Verify the Service status
Once completed with the installation verify he service status on replica node.
[root@idm2 ~]# ipactl status
Directory Service: RUNNING
krb5kdc Service: RUNNING
kadmin Service: RUNNING
named Service: RUNNING
httpd Service: RUNNING
ipa-custodia Service: RUNNING
pki-tomcatd Service: RUNNING
ipa-otpd Service: RUNNING
ipa-dnskeysyncd Service: RUNNING
ipa: INFO: The ipactl command was successful
[root@idm2 ~]#Replica Verification
To list and verify the replica jump to the master server or this can be fetched from replica as well.
[root@idm1 ~]# ipa-replica-manage list
idm1.lincls.linuxsysadmins.local: master
idm2.lincls.linuxsysadmins.local: master
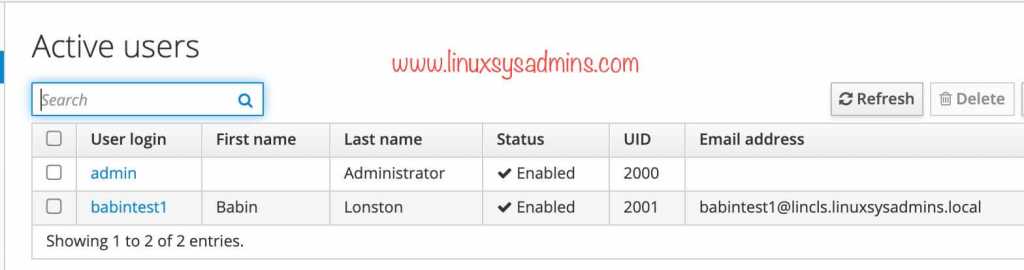
[root@idm1 ~]#To confirm the replication working fine, Add a user in master and verify from the replica.
If you need to create the same from command line use below command with options.
# ipa user-add --first=Babin --last=Lonston --password babintest1[root@idm1 ~]# ipa user-add --first=Babin --last=Lonston --password babintest1
Password:
Enter Password again to verify:
Added user "babintest1"
User login: babintest1
First name: Babin
Last name: Lonston
Full name: Babin Lonston
Display name: Babin Lonston
Initials: BL
Home directory: /home/babintest1
GECOS: Babin Lonston
Login shell: /bin/sh
Principal name: babintest2@LINCLS.LINUXSYSADMINS.LOCAL
Principal alias: babintest2@LINCLS.LINUXSYSADMINS.LOCAL
User password expiration: 20200228124006Z
Email address: babintest1@lincls.linuxsysadmins.local
UID: 2002
GID: 2002
Password: True
Member of groups: ipausers
Kerberos keys available: True
[root@idm1 ~]# Back to replica server and verify the newly added user.
[root@idm2 ~]# id babintest1
uid=2002(babintest1) gid=2002(babintest1) groups=2002(babintest1)
[root@idm2 ~]#
[root@idm2 ~]# getent passwd babintest1
babintest1:*:2002:2002:Babin Lonston:/home/babintest1:/bin/bash
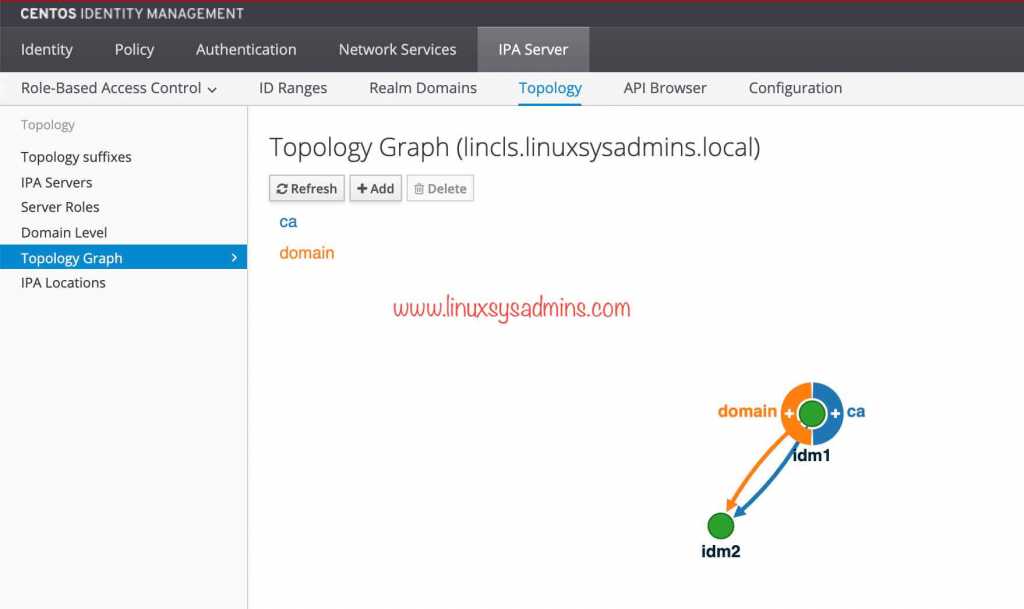
[root@idm2 ~]#Topology Graph of Replica setup
Few more information about the setup.
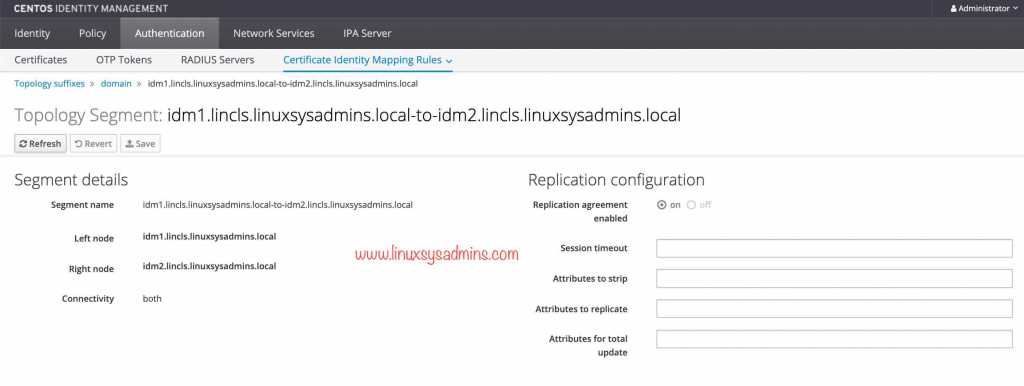
Tunning replication configuration can be done from Authentication –> Certificate Identity Mapping Rules –> Topology Suffixes –> domain.
Removing a Replica from master
In case, if we require to remove a replica from your setup it’s simple to remove by running a few commands.
[root@idm1 ~]# kinit admin
Password for admin@LINCLS.LINUXSYSADMINS.LOCAL:[root@idm1 ~]# klist
Ticket cache: KCM:0
Default principal: admin@LINCLS.LINUXSYSADMINS.LOCAL
Valid starting Expires Service principal
02/28/20 13:31:14 02/29/20 13:31:12 krbtgt/LINCLS.LINUXSYSADMINS.LOCAL@LINCLS.LINUXSYSADMINS.LOCAL
[root@idm1 ~]#[root@idm1 ~]# ipa-replica-manage list
idm1.lincls.linuxsysadmins.local: master
idm2.lincls.linuxsysadmins.local: master
[root@idm1 ~]#[root@idm1 ~]# ipa-replica-manage del idm2.lincls.linuxsysadmins.local
Updating DNS system records
ipa: WARNING: Failed to cleanup idm2.lincls.linuxsysadmins.local DNS entries: no matching entry found
ipa: WARNING: You may need to manually remove them from the tree
Deleted IPA server "idm2.lincls.linuxsysadmins.local"
[root@idm1 ~]# Finally, Uninstall the who set up.
# ipa-server-install --uninstallThat’s it we have completed with setting up a replica and removing a replica.
Conclusion
This guide walks through setting up a FreeIPA or IDM replica by following the above steps. Let’s come up with more articles related to FreeIPA and IDM server. Subscribe to our newsletter and stay tuned for more Linux how-to guides.
Hi Babin,
Thanks for your article. Already i made IPA replica successfully from master IPA. Now i wanna declare my replica as master node. Can you please give me some reference how i can do that?
Hello Babin,
First of all, I would like to thank you for the FreeIPA installation. My installation is successful.
BTW, do you know how to integrate Samba file server with IDM step by step? If yes, grateful if you could send me the docs. I followed the steps on this link “https://www.freeipa.org/page/Howto/Integrating_a_Samba_File_Server_With_IPA” but the samba file server did not work with the IPA server. For instance, I could not access a shared folder using the IPA User ID.
Thanking you in advance,
Owen
Thanks a lot Babin. You are truly awesome. I just loved the way you’ve describe each and every steps.
I would like to add couple more things here for someone who is new to this.
– AD and IDM must be in separate domain. Trust is not configurable if AD and IDM reside on the same domain
– RedHat IDM has 3 components.
– Trust controller, which is responsible for maintaining the trust between two realms.
– Trust agent – Trust agent can only leverage that trust and as a prat of that they can perform authentication lookup against active directory
– idm replica
–> RHEL client server first join IDM domain
–> The the IDM server contacts with one of the domain controller in AD since where the user actually lives.
–> then AD will send back a kerberos ticket back to IDM and then the user is able to authenticate.
–> one thing to note here that those credentials can be cached on idm and that is also a configurable settings.
Hi, Babin,
Thanks so much for your reply. In the end, it seems I had some sort of issue with one of the IPA servers. I am far from an expert on the subject so I don’t know exactly what was wrong, but when I would attempt to access the CA certificates in the GUI or via CLI on idm1, I would get a failure, even before attempting any migrations/upgrades. Fortunately, idm2 was fine, so I started the process over again with idm1 instead of idm2. In other words, I removed idm1 from replication and uninstalled it, then used a fresh CentOS8 VM and installed the replica on idm1, leaving idm2 untouched. That worked. Then, I just repeated the process on idm2 and everything is upgraded to CentOS8 now.
Thanks again!
Hey, Babin!
I have two FreeIPA servers in my lab running CentOS7, and I want to upgrade them to CentOS8. My intention was to remove the replica using steps similar to your section “Removing a Replica from master”. The removal seems to go well, but then I rebuild the replica with CentOS8 (fresh install, not an upgrade) and the replica fails to install.
To test, I restored both servers from a snapshot (back to the working replicated config) and tried again, but this time I tried to reinstall the replica without rebuilding the server. Still, I had problems.
Any ideas on what to try?
Dear Mattew Secaur,
Could you please confirm the version of FreeIPA you are running in CentOS7? And the version you are trying with installing on CentOS 8? Suspect it could be because of version using in replica end is different than the IDM server. As per the prerequisites of installing Replica, The replica and the master server must be running the same version of FreeIPA.
So, I have removed my old setup (CentOS 7) and build the lab on CentOS 8.2.2004 (Core) with IPA version 4.8.4-7. This can be installed from the default AppStream.
Thanks & Regards,
Bobin Lonston
@Matthew Secaur,
I’m wrong in my previous reply. The higher version of IPA can be run in a replica on CentOS 8.2. To confirm the same, quickly deployed two CentOS 7.8 based IPA servers.
[root@idm1 ~]# cat /etc/redhat-release
CentOS Linux release 7.8.2003 (Core)
[root@idm1 ~]#
This is the version of IPA using in CentOS 7.8 based servers.
FYI, when installing skipped the package ipa-server-trust-ad and disabled the SELinux as well. (Disabled, because this gave me some error)
[root@idm1 ~]# ipa –version
VERSION: 4.6.6, API_VERSION: 2.231
[root@idm1 ~]#
Added the idm2 as replica.
[root@idm1 ~]# ipa-replica-manage list
idm1.linuxsysadmins.local: master
idm2.linuxsysadmins.local: master
[root@idm1 ~]#
Verified the functionality and everything works. Once confirmed, deleted the replica (idm2).
[root@idm1 ~]#
[root@idm1 ~]# ipa-replica-manage del idm2.linuxsysadmins.local
Updating DNS system records
ipa: ERROR: unable to resolve host name idm2.linuxsysadmins.local. to IP address, ipa-ca DNS record will be incomplete
———————————————-
Deleted IPA server “idm2.linuxsysadmins.local”
———————————————-
[root@idm1 ~]#
[root@idm1 ~]# ipa-replica-manage list
idm1.linuxsysadmins.local: master
[root@idm1 ~]#
Deployed a fresh CentOS 8.1.911 from the template. (Not updated any packages)
[root@idm2 ~]# cat /etc/redhat-release
CentOS Linux release 8.1.1911 (Core)
[root@idm2 ~]#
Installed the IDM packages by excluding adtrust.
# yum module install idm:DL1/{dns,server,client} -y
The IPA version is greater than version in idm1 server { (RHEL 7.8) , (VERSION: 4.6.6, API_VERSION: 2.231) }
[root@idm2 ~]# ipa –version
VERSION: 4.8.4, API_VERSION: 2.235
[root@idm2 ~]#
Joined the replica.
# ipa-replica-install –principal admin –admin-password Redhat@123 –no-host-dns –setup-ca –setup-dns –setup-kra –no-forwarders –force-join
[6/7]: creating replica keys
[7/7]: configuring ipa-dnskeysyncd to start on boot
Done configuring DNS key synchronization service (ipa-dnskeysyncd).
Restarting ipa-dnskeysyncd
Restarting named
Updating DNS system records
Global DNS configuration in LDAP server is empty
You can use ‘dnsconfig-mod’ command to set global DNS options that
would override settings in local named.conf files
The ipa-replica-install command was successful
[root@idm2 ~]#
Joined successfully. Verified from GUI as well. all the functionality are working fine.
[root@idm1 ~]# ipa-replica-manage list
idm1.linuxsysadmins.local: master
idm2.linuxsysadmins.local: master
[root@idm1 ~]#
[root@idm1 ~]# date
Sat Jul 18 11:58:06 +04 2020
[root@idm1 ~]#
[root@idm1 ~]#
Tried with uninstalling the IPA from replica (idm2)
# ipa-server-install –uninstall
Took a reboot, Once it up. Done a yum update.
[root@idm2 ~]# cat /etc/redhat-release
CentOS Linux release 8.2.2004 (Core)
[root@idm2 ~]#
[root@idm2 ~]# date
Sat Jul 18 12:14:18 +04 2020
[root@idm2 ~]#
Started to join the replica
# ipa-replica-install –principal admin –admin-password Redhat@123 –no-host-dns –setup-ca –setup-dns –setup-kra –no-forwarders –force-join
[6/7]: creating replica keys
[7/7]: configuring ipa-dnskeysyncd to start on boot
Done configuring DNS key synchronization service (ipa-dnskeysyncd).
Restarting ipa-dnskeysyncd
Restarting named
Updating DNS system records
Global DNS configuration in LDAP server is empty
You can use ‘dnsconfig-mod’ command to set global DNS options that
would override settings in local named.conf files
The ipa-replica-install command was successful
[root@idm2 ~]#
[root@idm2 ~]# date
Sat Jul 18 12:22:48 +04 2020
[root@idm2 ~]#
[root@idm2 ~]# ipa –version
VERSION: 4.8.4, API_VERSION: 2.235
[root@idm2 ~]#
[root@idm2 ~]# cat /etc/redhat-release
CentOS Linux release 8.2.2004 (Core)
[root@idm2 ~]#
[root@idm1 ~]# ipa-replica-manage list
idm1.linuxsysadmins.local: master
idm2.linuxsysadmins.local: master
[root@idm1 ~]#
[root@idm1 ~]# date
Sat Jul 18 12:24:01 +04 2020
[root@idm1 ~]#
Everything looks fine.
Thanks & Regards,
Bobin Lonston